I gave away my Dell XPS 10 tablet. It was a Dell. I just didn’t like it. Also, this new one has a mobile network connection.
It looks much nicer than the Dell.
Nokia recommends Windows RT 8.1 which by complete coincidence is also the only operating system that works on the tablet. In contrast to x86 computers, ARM computers are not standardised and there is no single model of one maker that compatibility is based on (like the IBM PC). Hence operating systems are ported not just to the ARM platform but to the ARM platform and specific computers. I am thinking Linux and Android support the greatest selection of ARM-based computers. Windows RT supports very specific computers only and is always pre-installed.
Work easy. Play hard. Windows
I have no idea what that even means. I don’t think a tablet can be used for work. It simply isn’t the right formfactor. And a Windows RT tablet cannot be used to play. There simply aren’t the right games available.
Windows RT is not a bad operating system. In fact all things considered it is very good for tablets. But it’s not an app bonanza. The BlackBerry World store is better. And they are far behind iOS and Android.
My post on the Dell XPS 10 describes some of the advantages of Windows RT over iOS. Now that Microsoft Office is apparently available on the iPad, the two biggest advantages shrink to one, although I would still count Office as an advantage since it comes pre-installed. The other advantage remains. Windows RT comes with Powershell and also allows Powershell remote access.
Typing winrm quickconfig -force sets up Powershell remoting and lies about opening all the necessary ports in the firewall. Some experimenting will discover that the firewall rule winrm configured is for the domain profile. Windows RT devices cannot be added to a domain. The rule needs to be set up in the public profile.
Finding the firewall rule is as straightforward as things always are in Microsoft Windows.
Typing Get-NetFirewallRule|?{$_.displayname -like "*remote management*"}|%{$_.displayname} gets a list of rules, one of which is the one we want.
Windows Firewall Remote Management (RPC)
Windows Firewall Remote Management (RPC-EPMAP)
Windows Firewall Remote Management (RPC)
Windows Firewall Remote Management (RPC-EPMAP)
Windows Remote Management (HTTP-In)
Windows Remote Management (HTTP-In)
Windows Remote Management - Compatibility Mode (HTTP-In)
Windows Remote Management - Compatibility Mode (HTTP-In)
In fact the one we want is one of the Windows Remote Management (HTTP-In).
Let’s look at those.
$rules=Get-NetFirewallRule|?{$_.displayname -like "windows remote management (http-in)”}
Have the two rules displayed: $rules
Name : WINRM-HTTP-In-TCP-NoScope
DisplayName : Windows Remote Management (HTTP-In)
Description : Inbound rule for Windows Remote Management via WS-Management. [TCP 5985]
DisplayGroup : Windows Remote Management
Group : @FirewallAPI.dll,-30267
Enabled : True
Profile : Domain
Platform : {}
Direction : Inbound
Action : Allow
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : NotApplicable
PolicyStoreSource : PersistentStore
PolicyStoreSourceType : Local
Name : WINRM-HTTP-In-TCP
DisplayName : Windows Remote Management (HTTP-In)
Description : Inbound rule for Windows Remote Management via WS-Management. [TCP 5985]
DisplayGroup : Windows Remote Management
Group : @FirewallAPI.dll,-30267
Enabled : False
Profile : Public
Platform : {}
Direction : Inbound
Action : Allow
EdgeTraversalPolicy : Block
LooseSourceMapping : False
LocalOnlyMapping : False
Owner :
PrimaryStatus : OK
Status : The rule was parsed successfully from the store. (65536)
EnforcementStatus : NotApplicable
PolicyStoreSource : PersistentStore
PolicyStoreSourceType : Local
The exception rule for the Public profile is not enabled, but the Domain profile one is.
Let’s add the Private profile to the enabled rule. This stores the name of the rule we want in $rule:
$rule=$rules[0].name
This sets the rule to be applicable to the Domain and Private profiles:
Set-NetFirewallRule $rule -Profile Domain,Private
And this confirms that it worked:
(Get-NetFirewallRule $rule).Profile
It should show Domain, Private.
Now, I think when I did this on the Dell, I simply disabled the firewall. But the Lumia 2520 has a mobile network connection and you should never travel without a firewall. And pants. You should never travel without pants too.
File sharing is equally easily activated.
First, find the service responsible for file shares.
$s=Get-Service Server
Then set the service to autostart and start it.
$s|Set-Service -StartupType Automatic
$s|Start-Service
Obviously this needs a firewall rule. Luckily this time the rule already exists for the Private profile.
Get-NetFirewallRule|?{$_.displayname -like "file and printer sharing*smb*”}
It’s one of these.
Find the correct File and Printer Sharing (SMB-In) rule for the Private profile and enable it:
Enable-NetFirewallRule "{72B73B3A-86F3-4B84-BB51-7DDA93871840}”
Instead of 72B73B3A-86F3-4B84-BB51-7DDA93871840 use whatever number you find as the name of the rule you need. Don’t forget the brackets and quotes. It’s that easy! You probably want to enable Powershell remoting before you do all these things. Maybe deactivate the firewall until you have all the rules configured correctly.
Not I can finally copy screenshots from the tablet’s C$ share.
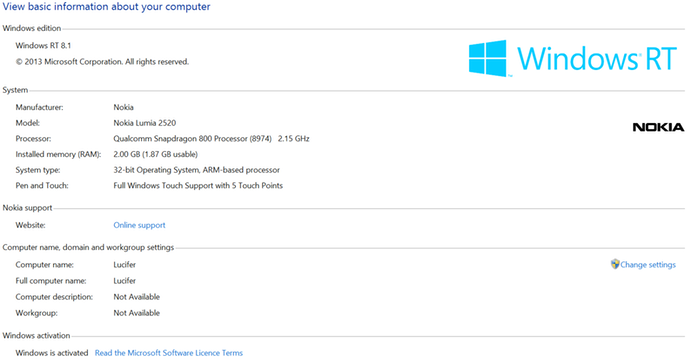
As all Windows RT tablets, the Lumia 2520 comes with Microsoft Office. Microsoft Office comes with Microsoft Outlook which is almost usable as an email program, if you are not very demanding. The iPad really comes with the better email program, but my RT tablet still has the big advantages in that it can be programmed on-the-fly using Powershell and be accessed over the network using file shares and Powershell remoting. If it had Remote Desktop connectivity as well, it would be awesome.
App choice is still abysmal. If this thing didn’t come with Office and Internet Explorer, it would be really useless.
Notable differences between Windows RT and Intel versions of Windows 8
- Windows RT cannot run applications compiled for x86 or x64
- It cannot run any unsigned applications, even for ARM
- It can therefore only run applications from Microsoft and WinRT apps from the Windows Store
- Because of that a lot of software that is generally available for Windows simply isn’t available for Windows RT
- There is no Hyper-V
- Large parts of the .NET framework and some PowerShell cmdlets are not accessible
- There is no Remote Desktop Connection server (although there is a Remote Desktop Connection client)
- ARM devices use less power than Intel computers
- Windows RT uses less memory than 64 bit Windows
- There is no NTVDM to run old DOS and 16 bit Windows programs like there is on Intel 32 bit Windows
- There is no deprecated POSIX subsystem (but who really cares)
- Windows RT includes Microsoft Office for free (including Outlook)
